Intro to Snyk UI
Welcome to the Snyk UI
~25mins estimatedWelcome to Snyk Training!
This course will help with all find, prioritize, and fix tasks available within the Snyk UI for Open Source, Code, Container, and IaC projects. This course includes 8 videos and several interaction and text pages that take approximately 30 minutes to complete.
If you prefer shorter, more focused courses, visit one of the following:
- Introduction to Snyk - a short course to help developers learn a few basic concepts and tasks for working in the Snyk developer security platform.
- Find and fix with Snyk Open source - a short learning path to help developers learn how to find, prioritize, and fix with Snyk on open source projects.
- Find and fix with Snyk Code - a short learning path to help developers learn how to find, prioritize, and fix with Snyk on code projects.
SSO login
When you log into Snyk, there are a few different choices for authentication. If your company is using single sign-on, make sure to use the SSO link. If you log in with a different authentication provider than the one used to create your Snyk account, you'll create a new account, and won't be logged into the correct Organization.
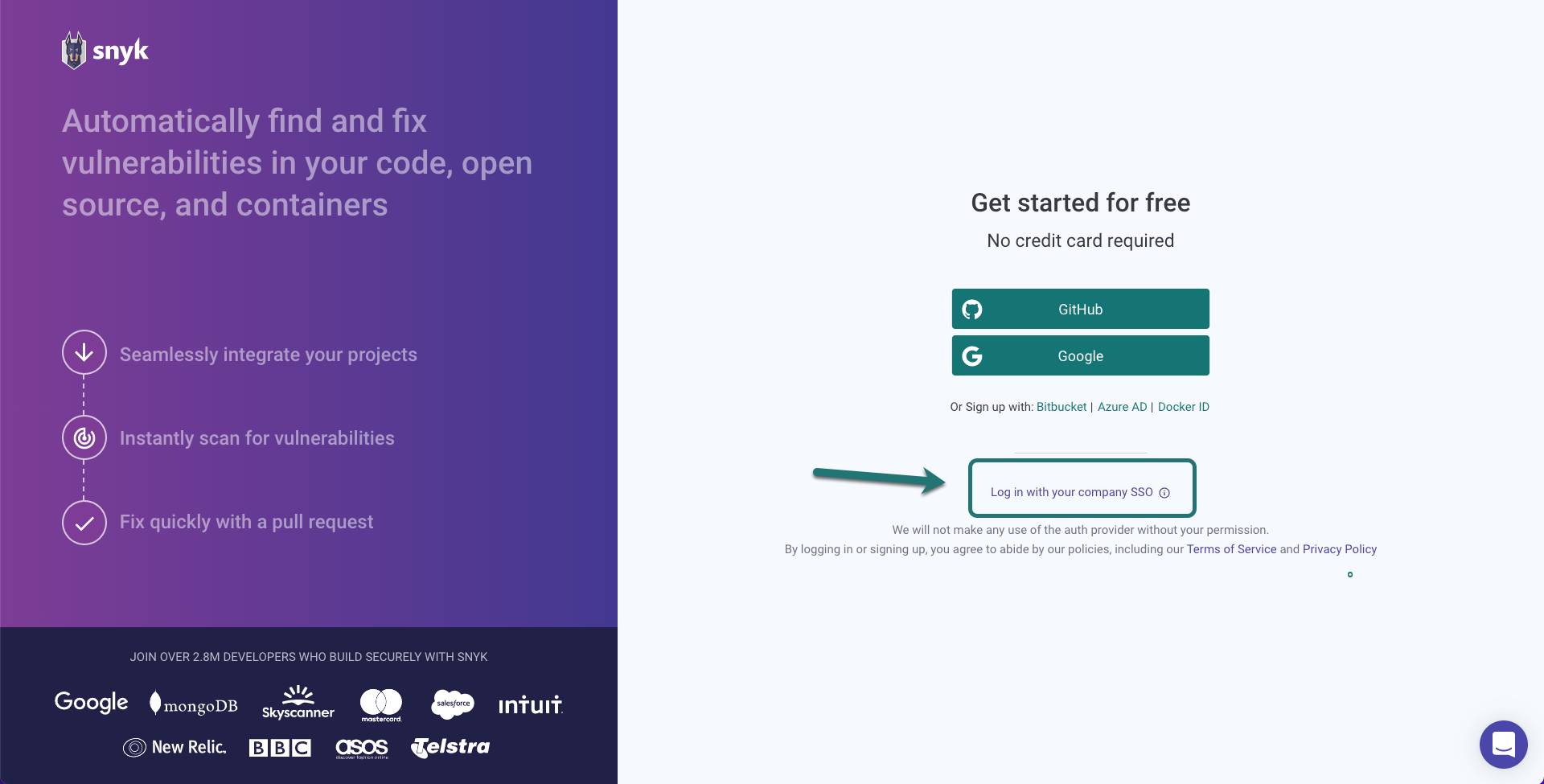
Request invitation
If your company requires an invitation to use Snyk, you may see a list of organizations when you log in for the first time via SSO. This means that you have not yet been invited. Select an Admin's name to start an email to request access to that Organization.
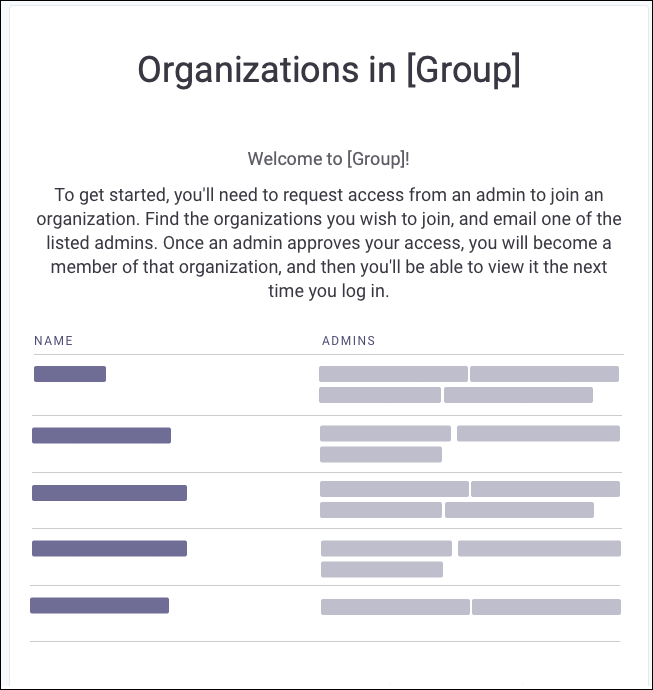
Changing Organizations
Organizations in Snyk control access to projects. The organization settings and policies also influence scan results, depending on which organization is used when adding a project.
Snyk shows your preferred organization by default when you log into the Snyk UI. Snyk also uses the settings for your preferred organization when you are testing a project locally using the CLI.
Add a project to current organization
This 1 minute video shows how to import a project from your connected source code manager.
Icon details for adding SCM projects
When adding projects with your source code manager, the following icons provide a little more detail about your projects:
 Private repository
Private repository
 Branched from another repository
Branched from another repository
 Has previously been imported to Snyk
Has previously been imported to Snyk
Snyk scanning concepts
In Snyk, a project is a scannable external item. Each target you want to scan, such as a Kubernetes cluster or GitHub repository, may include more than one project. Snyk scans different types of projects in different ways.
Open source projects
Snyk accesses the manifest and the build configuration files to identify Open Source dependencies.
Dockerfile projects
Snyk views the FROM statement to identify the base image.
Snyk predicts the potential vulnerabilities that will exist once the container has been built.
Note that scanning a Dockerfile is not equivalent to a container scan.
Scan built containers via the CLI or in the CI/CD pipeline.
Infrastructure projects
Snyk scans infrastructure files to search for misconfigurations. Analysis is based on industry standards of secure configurations.
Code projects
Snyk caches repository code for a one-time analysis.
Snyk only retains the file path, line, and column to any identified issues.
CLI projects
Snyk continuously monitors projects that have been added from the CLI via Snyk monitor.
About Dockerfile scans
Before you build an image, you can perform an easy and early scan of your Dockerfile to help surface base image vulnerabilities. The Snyk recommendations can help you choose the best base image for your project.
This light scan of the image snapshot can be a good early warning system.
There are other more comprehensive ways to fix issues in containers that will be covered in other courses.
The Projects page
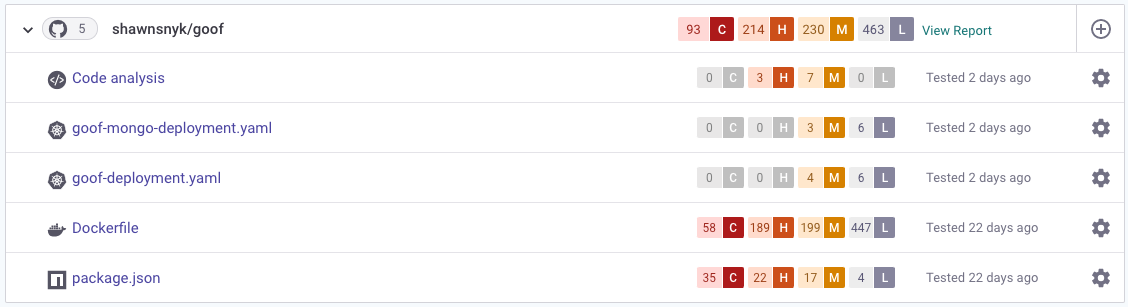
After adding your project, Snyk displays an overview of the project on the Projects page, including the number of critical, high, medium, and low vulnerabilities.
Expand the target to view the individual projects. For example, this GitHub repository includes five projects.
Understand Issue components
About dependencies
Applications may introduce known vulnerabilities either through direct or indirect dependencies.
A direct dependency is a package explicitly included in a project. An indirect dependency is not included directly in the project, but it is called by another dependency.
For example, in the following illustration, mongodb@3.5.9 is included directly in the project. At this time, it does not contain vulnerabilities itself. However, it references the package bl@2.2.0, which does contain vulnerabilities.

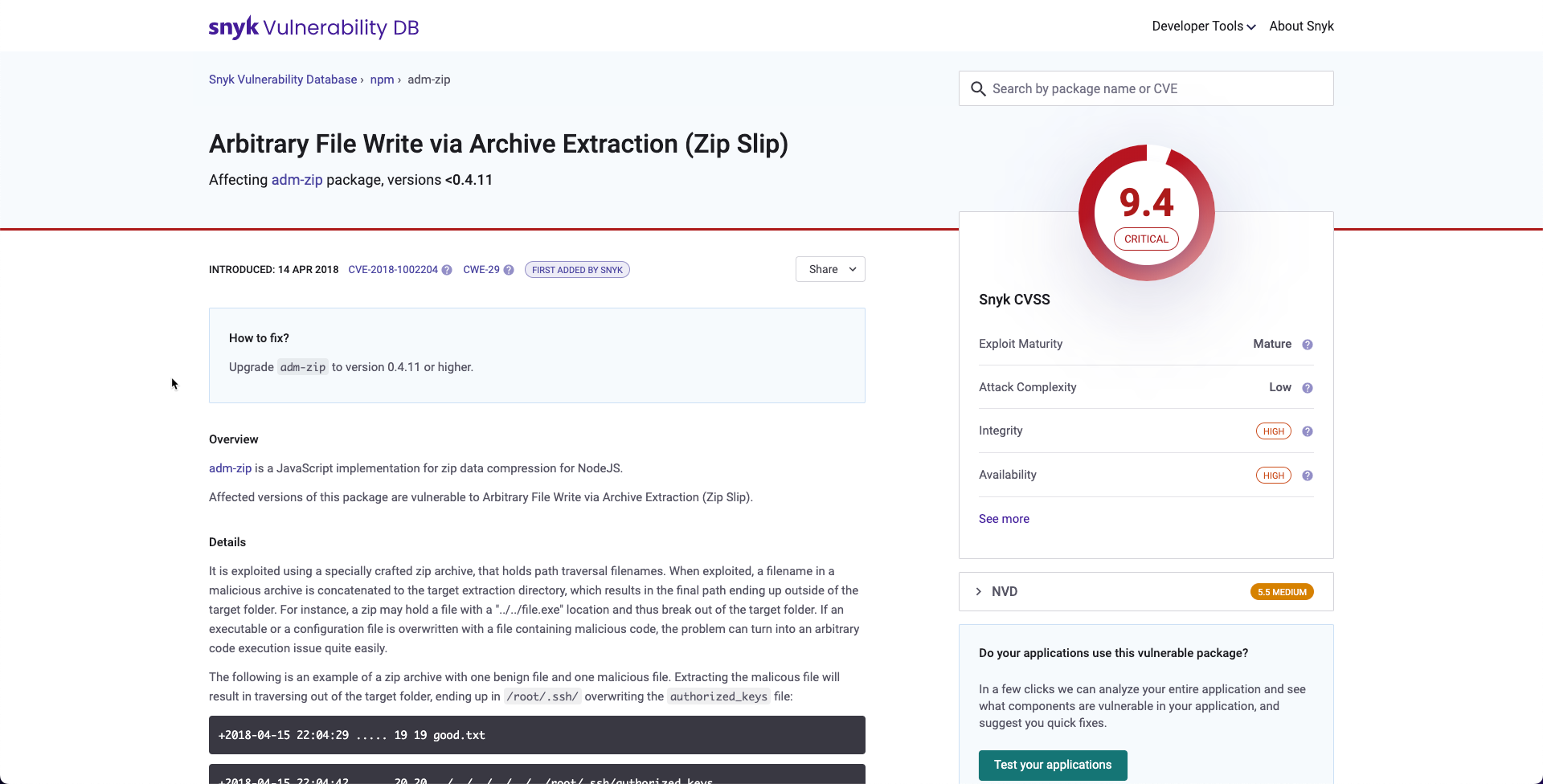
Snyk Vulnerability Database report
Select the link in the header of an issue to view the Snyk Vulnerability Database report for an issue.
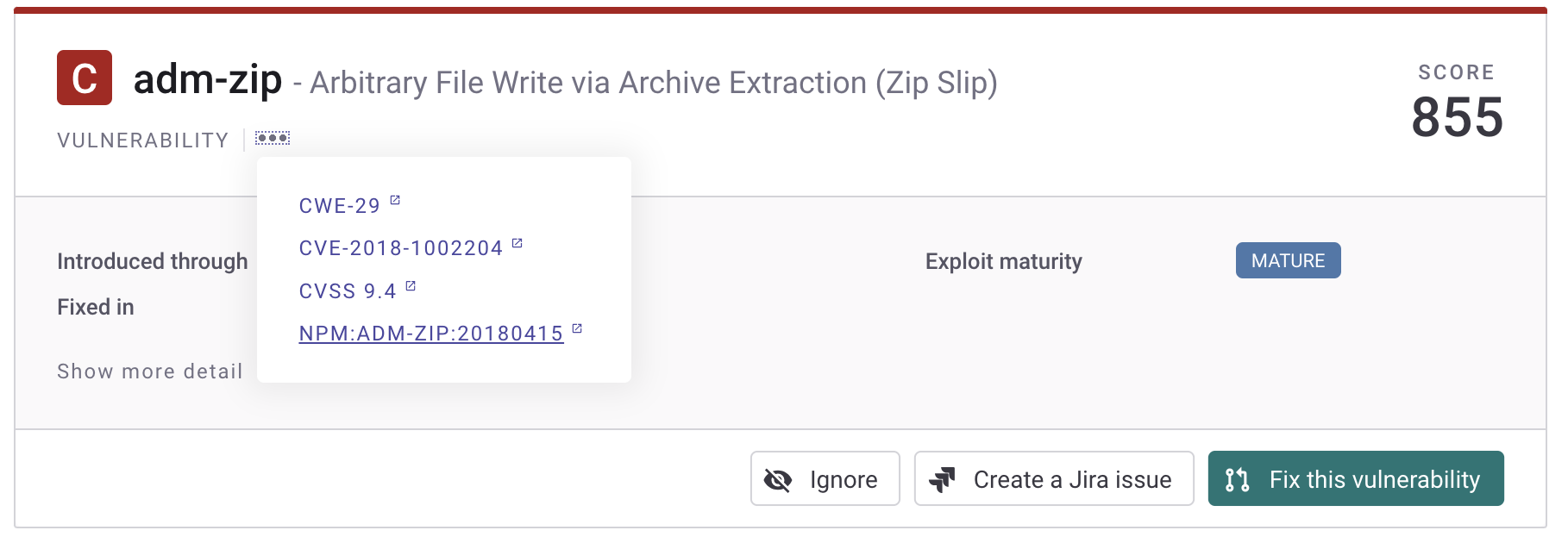
The Snyk Vulnerability Database includes details about the issue, the remediation advice, references, the components of the CVSS score, and the research credit and references.
Snyk Priority Score
Snyk processes and weighs several factors to produce the score for that issue.
The first half of the calculation is based on the CVSS score.
The second half of the calculation uses a proprietary algorithm that includes these factors:
- Severity
- The severity of an issue is calculated using the CVSS score for that issue.
- Exploit maturity
- The Snyk industry-leading security team determines the exploit maturity of an issue using manual and automated methods to track which vulnerabilities are exploitable, and to what extent.
- Reachability
- Snyk looks at the code paths called within a project to identify which vulnerabilities are reachable from the code.
- Fixability
- Snyk determines if a fix is available for the issue. Since developers must either fix the code themselves or use an alternative package when fixes are not available, Snyk gives issues with fixes higher priorities.
- Time
- Snyk gives an increased priority score to new vulnerabilities, which are likely to be an increased risk.
- Social trends
- Snyk monitors mentions of known vulnerabilities in Twitter, calculating the trend of tweets and reactions.
- Malicious packages
- Snyk prioritizes vulnerabilities originating from malicious packages.
Open source issue results
The Project page
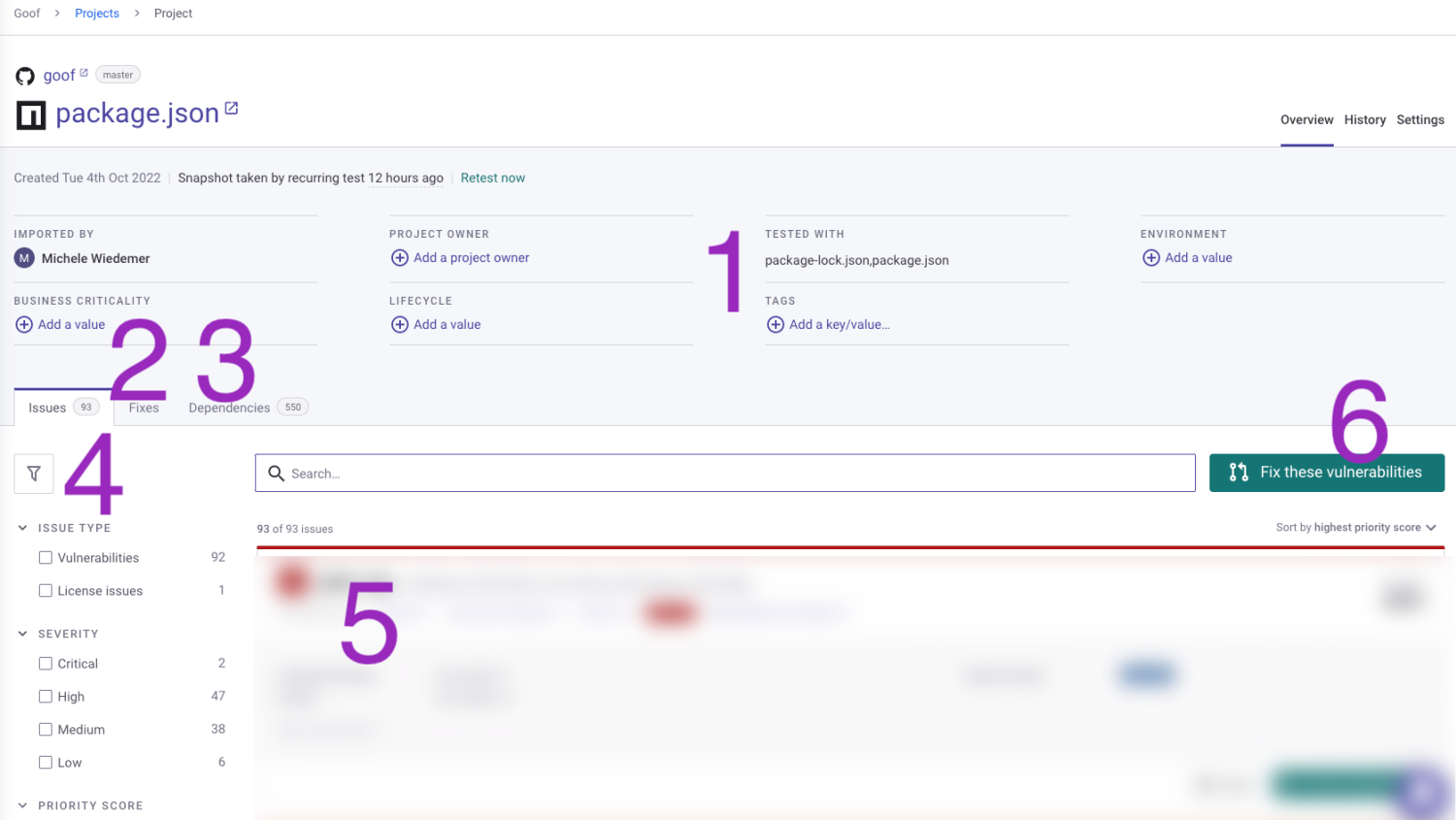
- Project attributes - Add attributes to the project to define the Business criticality, Lifecycle stage, Tags, and/or Environment.
- Fixes tab - The Fixes tab summarizes suggested fixes.
- Dependencies tab - The Dependencies tab shows the dependency tree with direct and indirect dependencies.
- Filters - Filters can help you prioritize the list of issues.
- List of issues - The issues identified for this project are listed with details for each issue. The total number of issues (according to current filters) is shown at the top of the list.
- Fix these vulnerabilities - The Fix these vulnerabilities button at the top of the issues list opens a fix pull request that includes all of the vulnerabilities in the list. Note that fix pull requests can also be opened for individual issues.
About the issue card
When you open a project, Snyk displays information about the identified issues. An issue card includes details about specific vulnerabilities or license issues with any recommended actions. The content and format of an issue card varies, depending on the type of project you open.
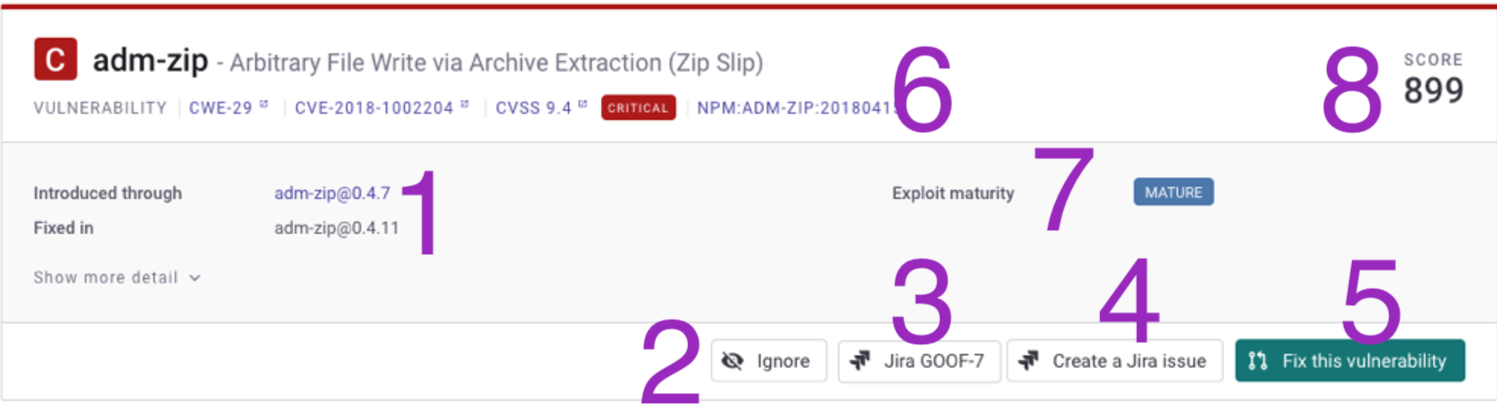
- Snyk scan results - Find out where issue was introduced and learn about recommended fix.
- Ignore - If enabled for current user, the Ignore button allows for temporarily or permanently ignoring this issue.
- Jira link - If a Jira ticket has been added for this issue, find the link directly to that ticket.
- Create Jira issue - If Jira has been integrated with the current organization, create a Jira ticket.
- Fix this vulnerability - If supported for your language/package manager, the Fix button allows you to open a PR for this issue.
- Exploit maturity Snyk identifies whether there is a published code exploit for this issue. Other considerations for your prioritization plan also appear in this area.
- Issue details - View details about the vulnerability and find links to review details in the Snyk Vulnerability database and more.
- Priority score - The Snyk Priority Score, based on the CVSS score and a propriety algorithm of other factors.
Snyk code issue results
The Project page
The Project page for project analyzed by Snyk Code includes details about that project.
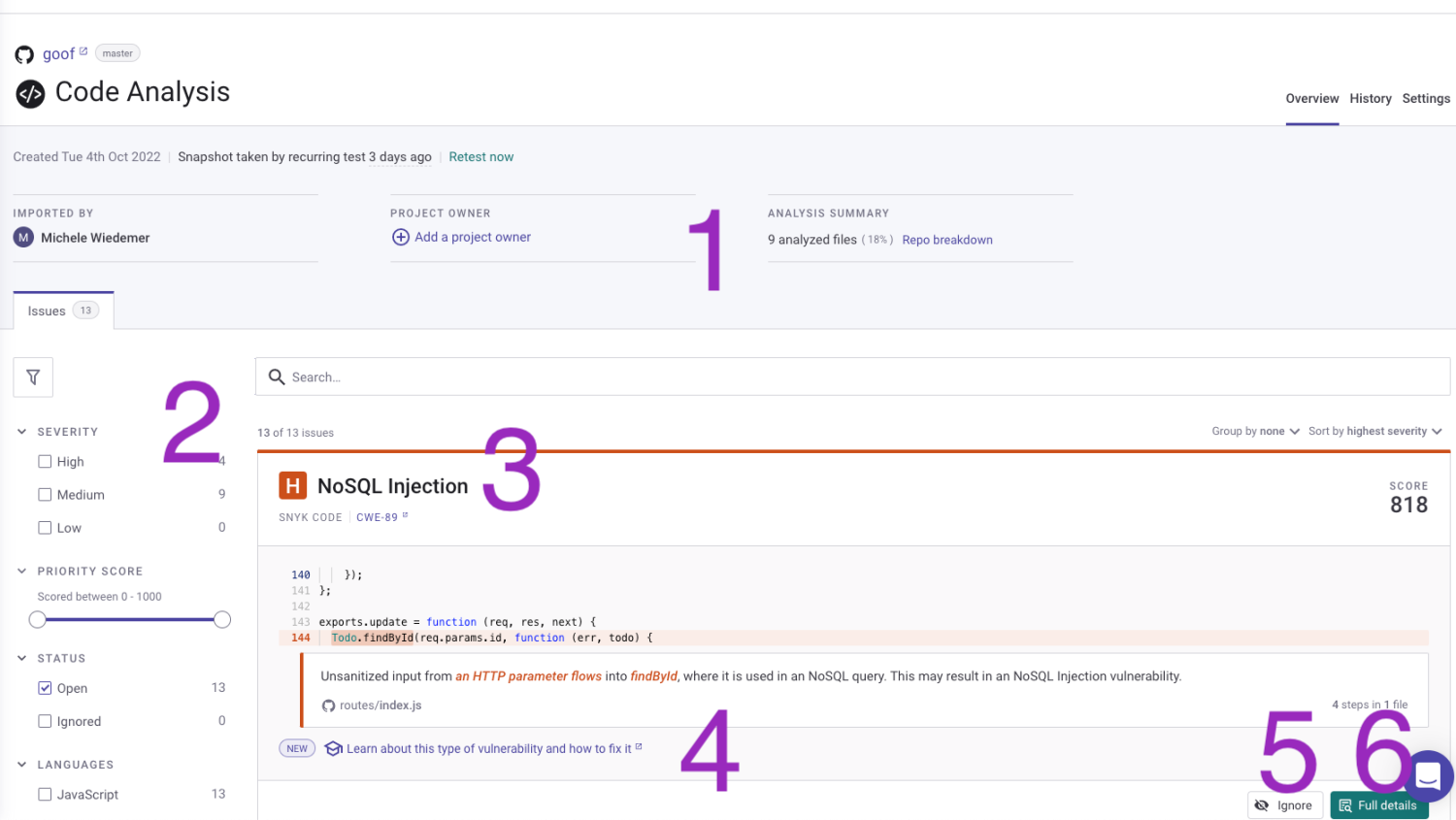
- Project attributes - Add attributes to the project to define the project owner.
- Filters - Filters can help you prioritize the list of issues.
- List of issues - The issues identified for this project are listed with details for each issue. The total number of issues (according to current filters) is shown at the top of the list.
- Learn - Open Snyk Learn in another window for related developer security lesson.
- Ignore issue - If enabled, ignore this issue temporarily or permanently.
- Full details - Review full details, including examples of how to fix the issue.
Review code issues
When you scan a code project file, Snyk Code provides information about potential security and quality issues and provides recommendations and sample remediation examples.
Container file issue results
The Project page
The Project page for a Dockerfile project includes details about that project.
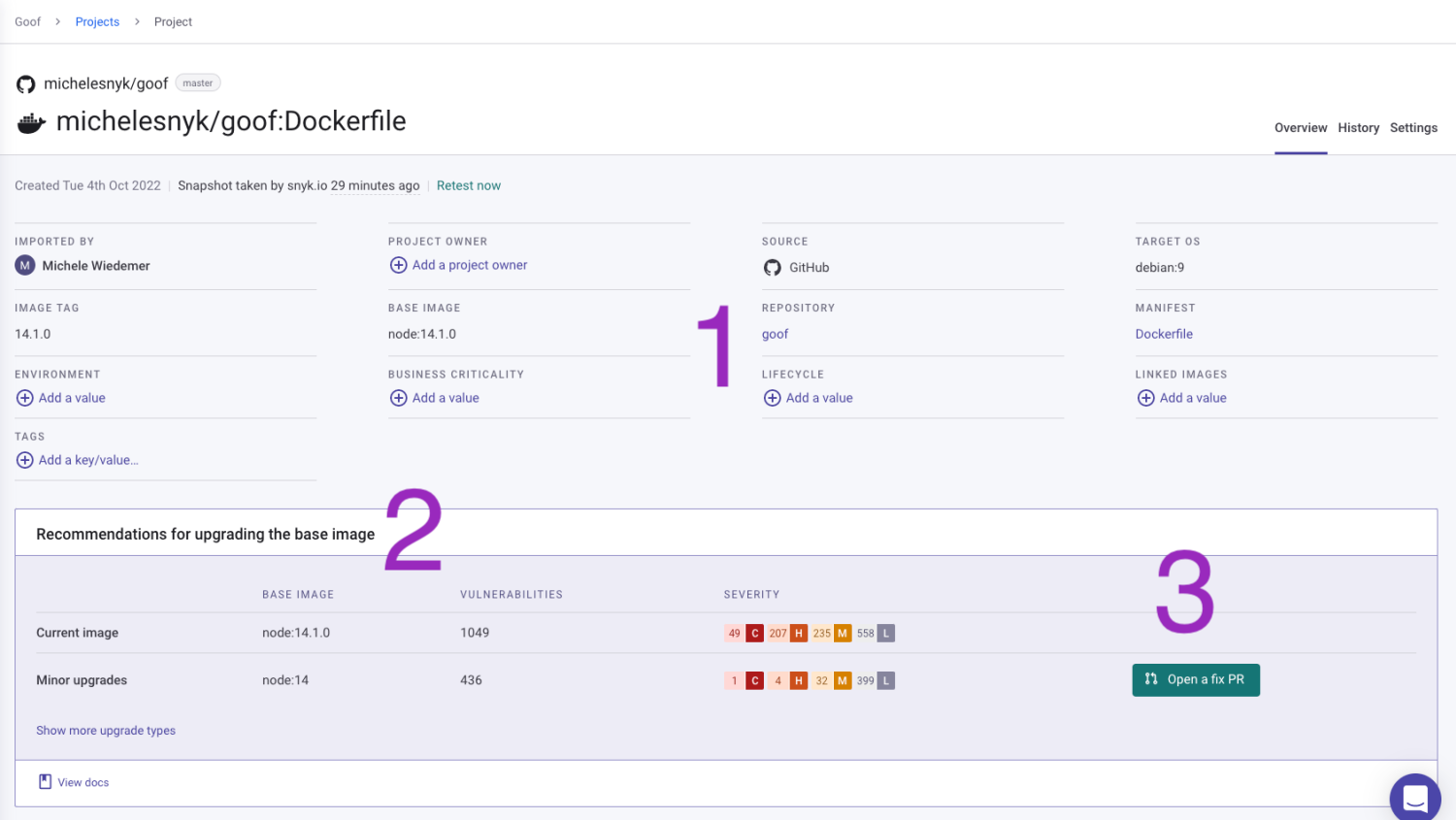
- Project attributes - Add attributes to the project to define the Project owner, Business criticality, Lifecycle stage, Tags, and/or Environment.
- Recommendations - Review an overview of number and severity of issues in the current image, as well as potential image upgrades.
- Open a Fix PR - Open a Fix PR to change the current base image to the selected recommendation.
Infrastructure as code file issue results
The Project page
The Project page for an infrastructure project includes details about that project.
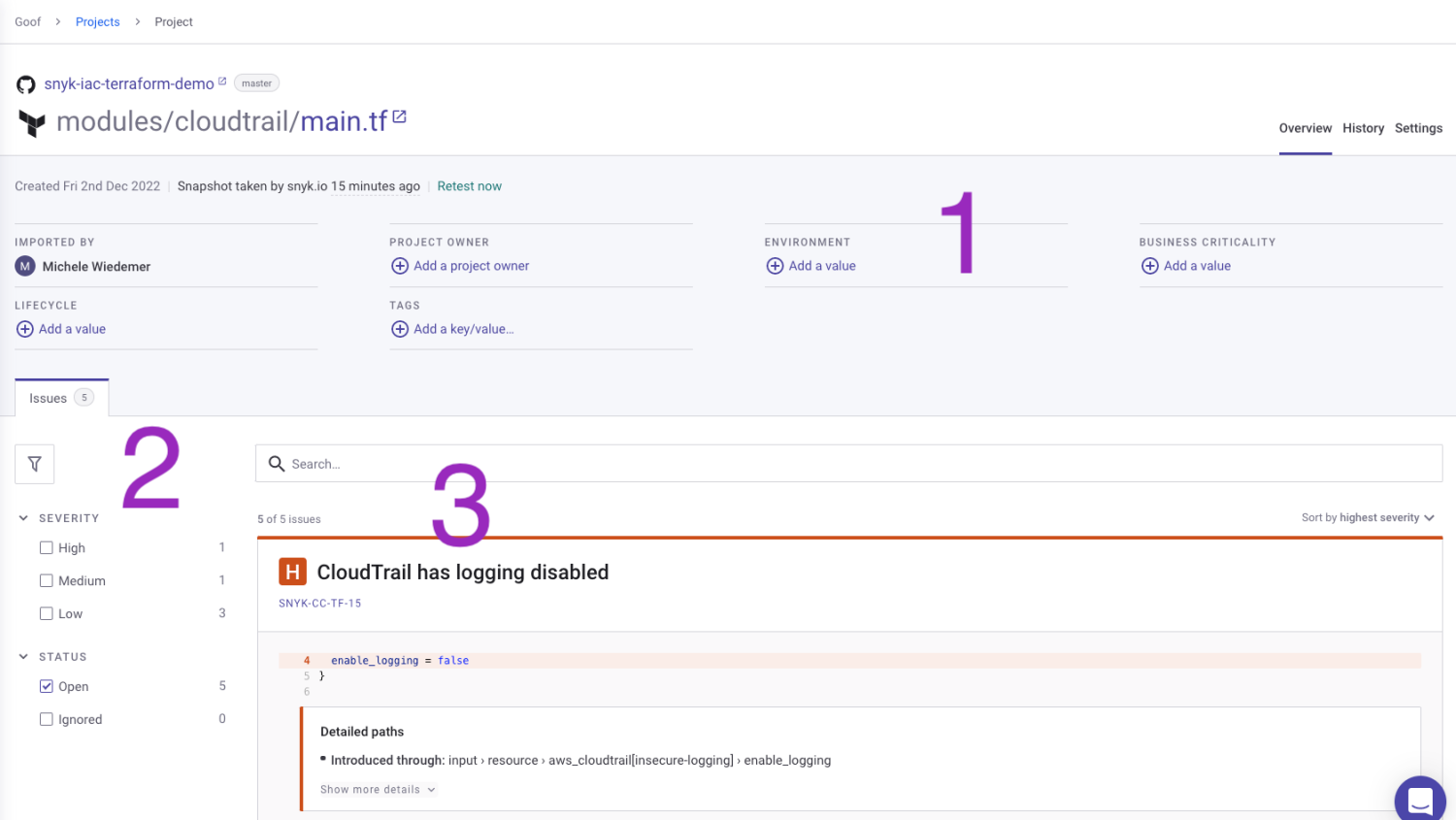
- Project attributes - Add attributes to the project to define the Project owner, Business criticality, Lifecycle stage, Tags, and/or Environment.
- Filters - Filters can help you prioritize the list of issues.
- List of issues - The line number and a description are listed for all issues identified for this project.
Review configuration issues
When you scan an infrastructure as code project file, Snyk IaC provides information about identified issues and provides suggestions for resolving issues.
Prioritizing issues
Snyk provides several ways to filter the list of issues, to help you prioritize the issues you want to address first.
Ignore issues via the Snyk UI
There are a few valid reasons for ignoring issues so they won't continue to appear in your list of issues. You can ignore an issue right from the issue card in the Snyk UI (if you have that permission). You can choose how long to ignore the issue and provide a rationale for the ignore.
Open a Fix PR
Depending on your language/package manager, you can open a Fix PR right from the Snyk UI.
Open a Jira issue
With the Jira integration connected to your Snyk account, you can initiate a Jira issue right from the Snyk UI.
Refer to the Snyk User Docs article Jira notifications setup for more details.
About Snyk Code scans
If Snyk Code has been enabled for your organization, Snyk performs static application security testing (SAST) on projects that include code in a supported language from a supported source code management system.
Snyk accesses files in the current project directory to identify vulnerabilities that could be exploited to attack the application.
Snyk tests the application by scanning the code without executing it, and reports on any vulnerabilities.
Snyk does not store code in the Snyk network or logs or use it for engine training purposes. The scan results do not contain original source code. The results include pointers to positions, plus meta-data on the version of the source code.
Open a fix for base image upgrade
You can open a Fix PR to change a base image in a Dockerfile right from the Snyk UI.