Intro to Snyk
Snyk interface and initial setup for first time user
Understand how projects fit into organizations, which may be part of a group.

Tenant
Enterprise customers, for scaling, have a robust way to organize access and reporting on the platform, the root of which is the tenant at the highest level. Each customer will generally have a single tenant. At this level, high-level analytics are available with Snyk AppRisk Pro, and Members allows management of users.
Groups
Groups are the top level of the Snyk account hierarchy (for Trials and Enterprise plans only).
Groups provide an overview of all included organizations and allows for configuration of some items like group-level service accounts and default notification settings.
License and security policies are defined at the group level for the organizations included in that group.
The usage of Groups varies by company.
- Most companies may have a single Group representing their company, providing roll-up reports and policies are shared among all their Organizations.
- Larger, more complex, companies may use Groups to represent each business or sub-company, when each one has its own policies, integrations, reporting needs, and people.
Organizations
Organizations are the way that Snyk controls project access and configuration.
Members of an organization gain access to all projects included within that organization.
Organizations are also where many integration settings and configurations are defined.
Targets and Projects
Once integrations are configured at the Organization level, Targets for scanning can be specified in a number of ways (UI, API, or monitored from an integration or CLI).
As an example, you may configure Github at the Organization level, and then in the web interface, specify to import a repository named "JuiceShop" as a Target for code repository scanning, and within it, there may be various Projects that are created, representing the open-source manifest file (package.json), or a Code Analysis Project and related security findings.
Projects are the components that Snyk tests, including the related configuration and metadata.
Projects live inside an organization.
Projects are the components that Snyk tests. Projects include related configuration and metadata. Each target you want to scan (repos, container images, Dockerfiles, configuration files, source code) may include more than one project.
Snyk Code
Source code files
Snyk analyzes your source code to identify the trace, file path, line, and column to any identified issues.
Snyk Open Source
Manifest files
For Open Source projects, Snyk accesses the manifest and build configuration files to identify Open Source dependencies (direct and indirect).
Snyk Container
Container images
You can build and test an image locally/at build with the Snyk CLI, or integrate with a registry and upload the results to the Snyk UI. This will provide a list of vulnerabilities and fixes for container and application open source packages that are in use. Additionally, Snyk can scan a Dockerfile from Git. When you scan a Dockerfile, Snyk views the FROM statement to identify the base image and predict potential vulnerabilities once that container has been built. Note that scanning a Dockerfile is not equivalent to a container scan (which is done in the CLI or in the CI/CD pipeline).
Snyk IaC
Infrastructure as code files
Snyk scans infrastructure files to search for misconfigurations, based on industry standards of secure configurations. Snyk shows a side-by-side code review interface.
Log into the correct organization
When you log into Snyk, there are a few different choices for authentication. If your company is using single sign-on, make sure to use the SSO link. If you log in with a different authentication provider than the one used to create your Snyk account, you'll create a new account, and won't be logged into the correct organization.
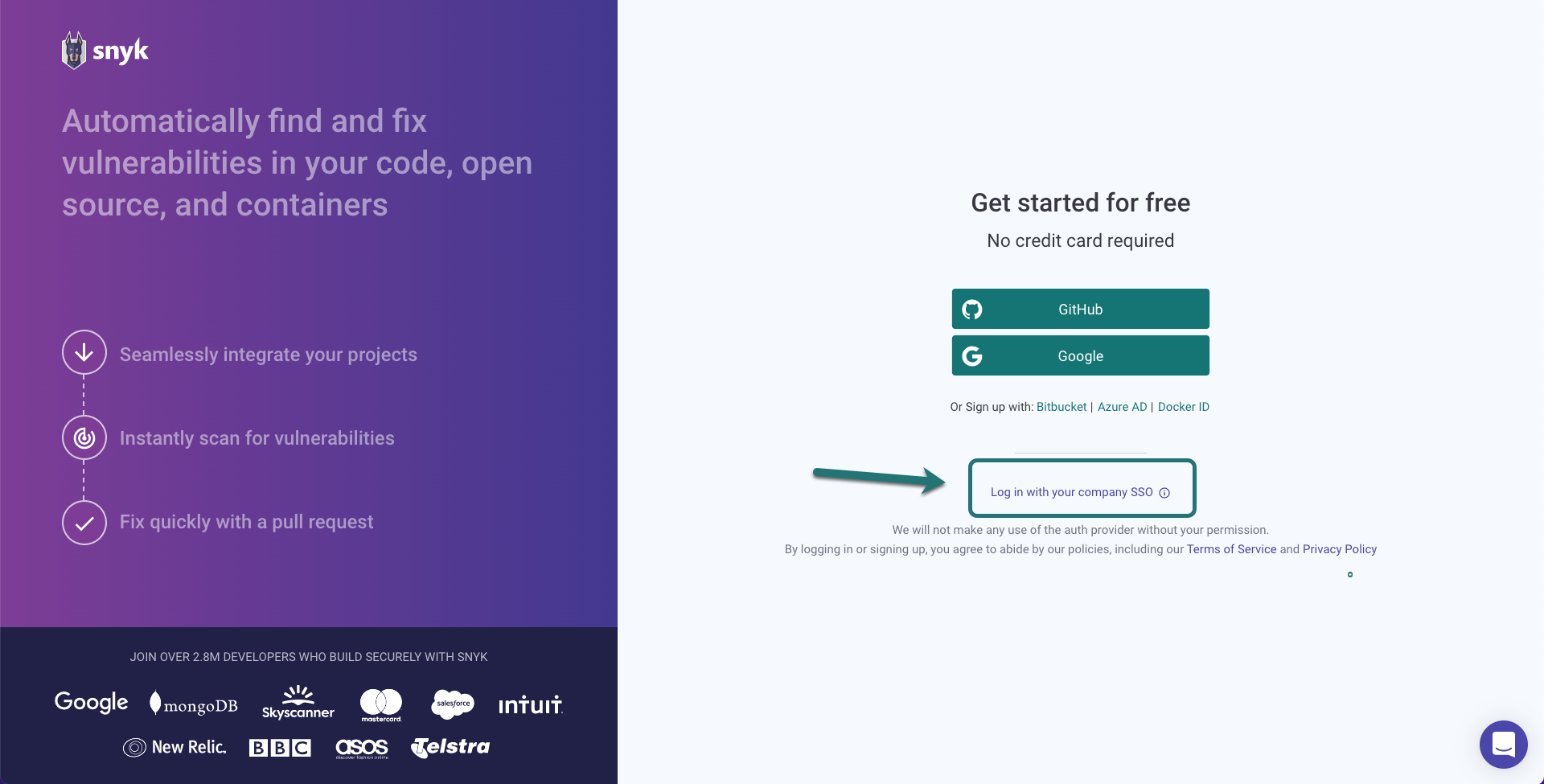
Change Organizations
Organizations in Snyk control access to projects. The organization settings and policies also influence scan results, depending on which organization is used when adding a project.
Snyk shows your preferred organization by default when you log into the Snyk UI. Snyk also uses the settings for your preferred organization when you are testing a project locally using the CLI.
Default notification settings come from the organization to which a project is added. Customize which notifications you get for which projects by changing your personal notification settings in the Snyk UI.
The Snyk Vulnerability Database includes details about issues, including the remediation advice, references, the components of the CVSS score, and the research credit and references.
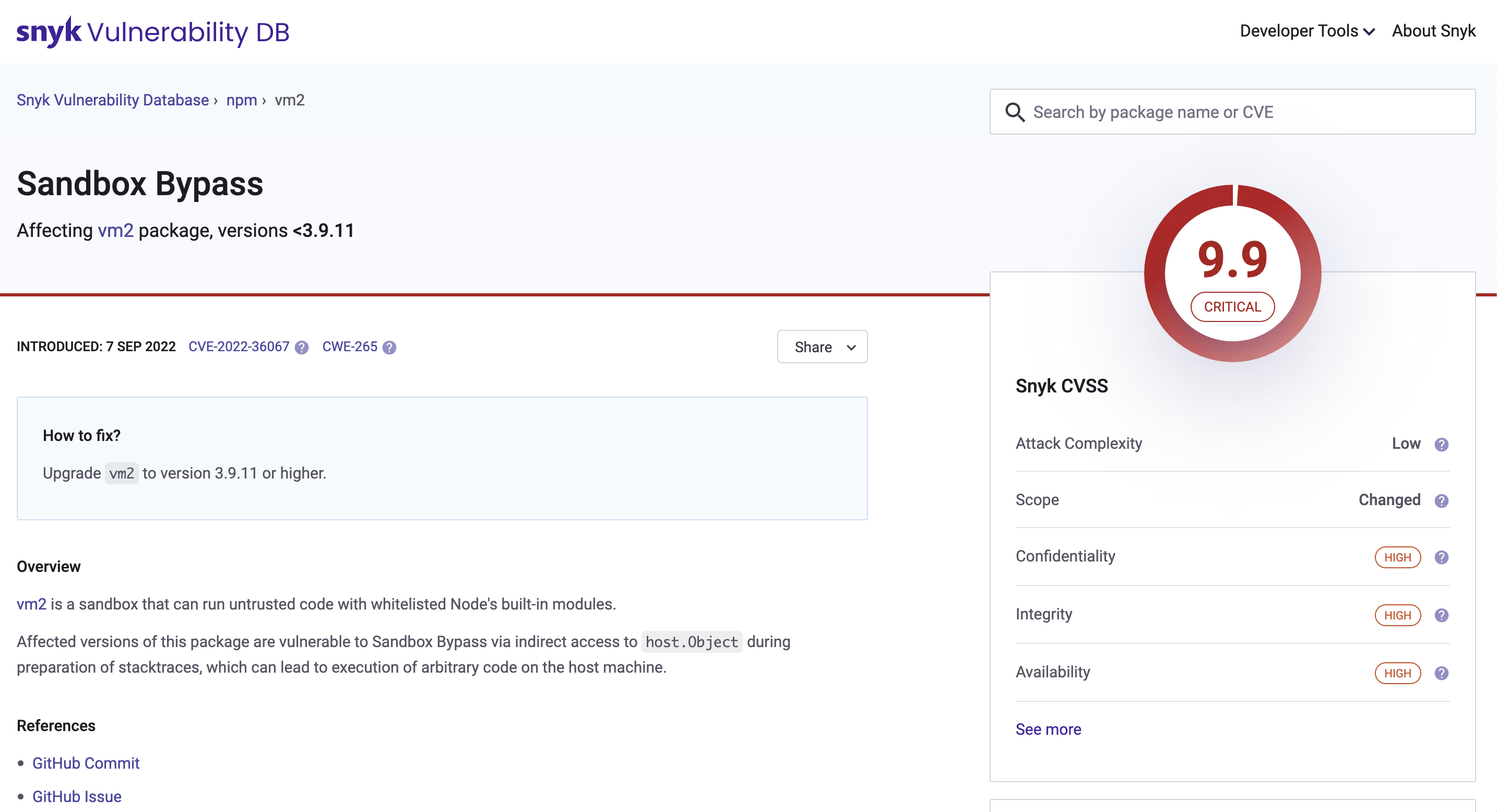
Within the Snyk UI, issues include a link in the header to view the Snyk Vulnerability Database data for that issue. When looking at the links, the last ID, shown here with the SNYK-JS prefix, provides access to the Vulnerability Database card.
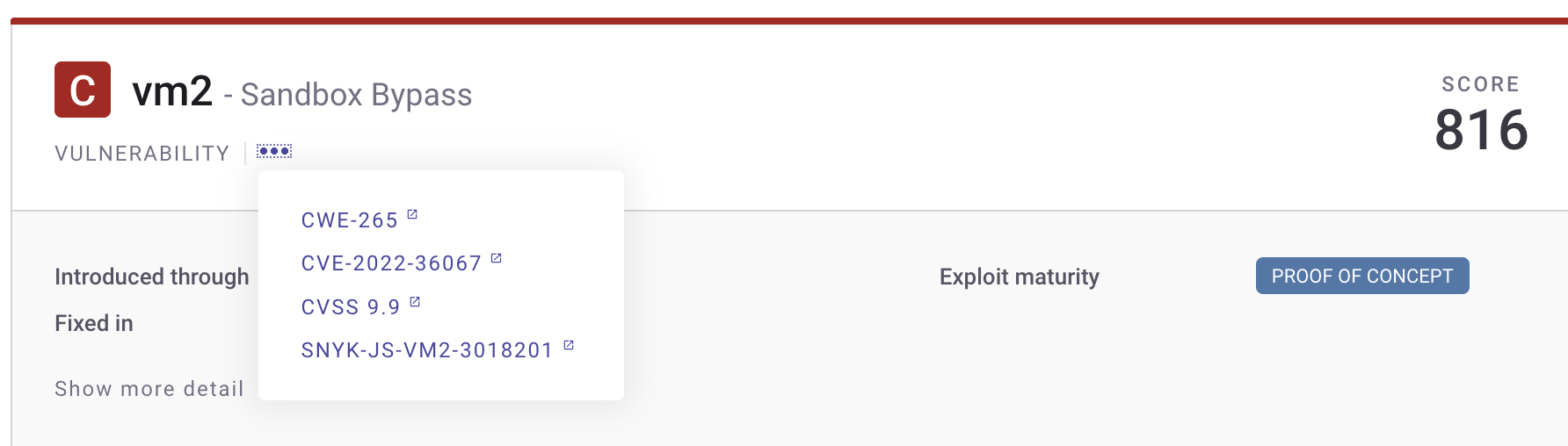
Snyk Guides
There are several Snyk Guides that provide best practices for getting started, implementing, and adopting Snyk according to a specific tech stack:
You can find more here: https://docs.snyk.io/scan-applications/supported-languages-and-frameworks